Reading Time: 4 minGRC and AI resilience refers to how Governance, Risk & Compliance frameworks are adapting to the rise of artificial intelligence.In 2025, the most resilient organizations embed AI oversight into every layer of governance ensuring transparency, accountability, and trust across automated decisions and intelligent risk systems. Introduction Artificial Intelligence is no longer a future concern it’s a present-day compliance challenge.As AI systems drive decisions across finance, healthcare, and cybersecurity, traditional GRC models struggle to keep up with algorithmic complexity, regulatory velocity, and ethical ambiguity. The question isn’t whether AI will reshape…
Read MoreTag: Zero Trust
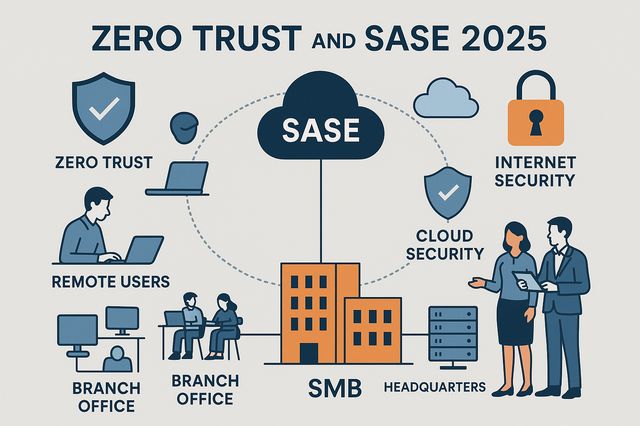
SASE 2025 | The Complete SECITHUB Guide for SMBs
Reading Time: 5 minSecure Access Service Edge is a cloud-native architecture that unifies networking and cybersecurity into a single platform. It delivers Zero Trust protection, fast connectivity, and policy consistency for users, devices, and data across all locations and clouds. Introduction In 2025, the network perimeter no longer exists.Users connect from anywhere, data flows across multiple clouds, and traditional firewalls can’t define the edge of trust.Organizations face one fundamental question:How can we stay secure, connected, and compliant without slowing down the business? The Origin of SASE Fragmentation and Complexity Before SASE, enterprises managed…
Read MoreISO 27001 in 2025 | From Certification to Real ROI
Reading Time: 6 minBy 2025, ISO 27001 has evolved from a compliance framework into a strategic growth engine.It enables SMBs and enterprises to build trust, accelerate deals, and strengthen governance through continuous monitoring, automation, and leadership alignment.Treating ISO 27001 as a business system not just an audit transforms compliance into a measurable driver of resilience and customer confidence. The New Era of Compliance | ISO 27001 as a Business Strategy By 2025, ISO 27001 has transformed from a regulatory checkbox into a strategic business advantage.What once served as a compliance framework for auditors…
Read MoreThe Complete SECITHUB Report for Choosing the Right Office Firewall | 2025 SMB Firewall Ranking & Buyer’s Guide
Reading Time: 6 minThe 2025 SECITHUB Firewall Ranking reveals how small and midsize businesses (SMBs) can select the best firewall for hybrid, cloud, and remote environments.Modern firewalls combine AI-driven threat detection, Zero Trust Network Access (ZTNA), and SASE architecture to protect users and data across all edges.Choosing the right solution Fortinet, Cisco Meraki, Sophos, Palo Alto, or WatchGuard means securing not just your network, but your business continuity in 2025 and beyond. Why SMB Firewall Decisions Matter in 2025 | The Small Business Gateway Is Under Attack In 2025, small and midsize businesses…
Read MoreZero Trust Access Management for SMBs in 2025 | Controlling Identity, Cloud, and Access
Reading Time: 5 minZero Trust Access Management (ZTAM) is the next evolution of identity and access control for small and midsize businesses.It replaces static trust with continuous verification ensuring every user, device, and session is authenticated in real time.In 2025, SMBs adopting Zero Trust reduce credential-based breaches, improve compliance readiness (ISO 27001, GDPR, PCI-DSS), and cut administrative overhead by up to 40% through automation and centralized identity governance. The Hidden Cost of Uncontrolled Identity In small and midsize businesses, access management is often invisible until something goes wrong.A single shared password, a forgotten…
Read MoreCloud NAC for SMBs in 2025 | A Zero Trust Strategy to Cut Downtime and IT Costs
Reading Time: 6 minCloud Network Access Control (Cloud NAC) is a cloud-based Zero Trust framework that manages and secures every device connecting to a business network whether wired, wireless, or remote.In 2025, SMBs use Cloud NAC to automate onboarding, verify device compliance, and isolate threats in real time.It reduces IT workload by up to 40%, eliminates unauthorized access, and ensures continuous compliance with regulations such as GDPR, HIPAA, and ISO 27001 all without on-premise servers or complex configuration. The Hidden Cost of Uncontrolled Access In most small and midsize businesses, network access happens…
Read MoreHow to Configure a Network Switch | Squeeze Out Maximum Security from Your SMB Network Equipment
Reading Time: 6 minConfiguring a network switch for SMB security means transforming it from a basic traffic device into an identity-aware, Zero Trust access layer.By applying VLAN segmentation, 802.1X network access control (NAC), and switch-hardening best practices (SSH, SNMPv3, BPDU Guard, DHCP Snooping, DAI), SMBs can eliminate internal threats, enforce least privilege, and monitor traffic effectively.A properly configured switch becomes not just a connection point but a policy enforcement engine at the network edge. A secure, segmented, Zero-Trust-ready access layer A modern switch shouldn’t just move packets it should enforce policy at the…
Read More