Configuring a network switch for SMB security means transforming it from a basic traffic device into an identity-aware, Zero Trust access layer.By applying VLAN segmentation, 802.1X network access control (NAC), and switch-hardening best practices (SSH, SNMPv3, BPDU Guard, DHCP Snooping, DAI), SMBs can eliminate internal threats, enforce least privilege, and monitor traffic effectively.A properly configured switch becomes not just a connection point but a policy enforcement engine at the network edge. A secure, segmented, Zero-Trust-ready access layer A modern switch shouldn’t just move packets it should enforce policy at the…
Read MoreDay: September 27, 2025
How to Build and Secure a Network Rack for SMB Offices | A Practical Guide
Building and securing a network rack for SMB offices means designing the physical and logical foundation of your IT environment where connectivity, stability, and security all meet.A well-planned rack ensures uptime, protects equipment, and supports business growth.Core best practices include: Proper capacity and airflow planningClear rack organization (patch panels → switches → servers → power) Strong physical access controls and monitoring Secure firmware, cabling, and labeling standards Ongoing audits, remote monitoring, and MSP oversight In 2025, your network rack isn’t just hardware it’s your business continuity engine. For small and…
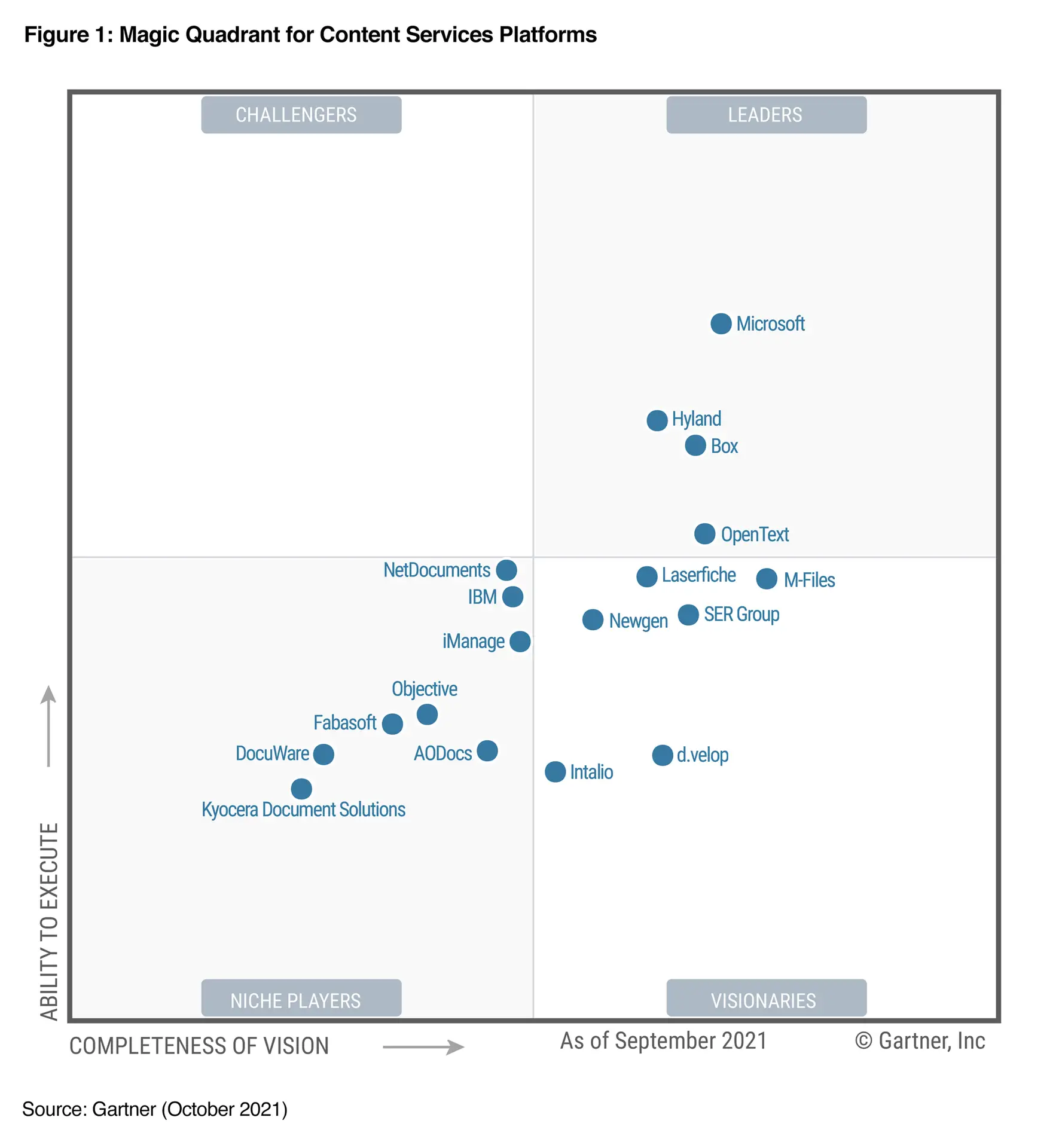
Read MoreHow to Read Gartner’s Magic Quadrants | Value, Limitations, and Practical Use for IT Leaders
Gartner’s Magic Quadrant is one of the most influential research tools for evaluating technology vendors.It ranks companies based on two key dimensions Ability to Execute (how well they deliver today) Completeness of Vision (how well they anticipate the future). However, while the Quadrant offers a useful snapshot of the competitive landscape, it can mislead when taken at face value.IT leaders should use it as a starting point for strategic evaluation not as the final decision-maker.True value comes from combining Gartner’s insights with hands-on testing, TCO analysis, and real-world fit to…
Read MoreSECITHUB Weekly Opinion | Why Intel Was Targeted by NVIDIA
In September 2025, NVIDIA invested $5 billion for a 4% stake in Intel, marking one of the most strategic semiconductor alignments in recent U.S. history.Unlike a simple financial transaction, this move reflects a national and industrial strategy: strengthening U.S. chip manufacturing, reducing dependence on Asian foundries, and securing the AI supply chain. For NVIDIA, it’s about diversifying production and influencing Intel’s foundry roadmap.For Intel, it’s validation and survival, as the world’s AI leader bets on its recovery.Beyond business, this signals a public-private alliance—a fusion of policy and profit to ensure…
Read More