Gartner’s Agentic AI Revolution (2025) redefines how technology excellence is measured.Instead of ranking vendors by vision and execution alone, Gartner now evaluates autonomy, trust, and governance assessing how safely AI systems act without human input.In cybersecurity, this marks a shift from “ability to execute” to “ability to execute responsibly”, where ethical AI and explainable decisions define true leadership. From Analyst Frameworks to Autonomous Intelligence | Agentic AI For more than two decades, Gartner’s Magic Quadrant has defined how the world evaluates technology.Its two legendary axes Vision and Execution have guided…
Read MoreCategory: Cyber Trends & Insights
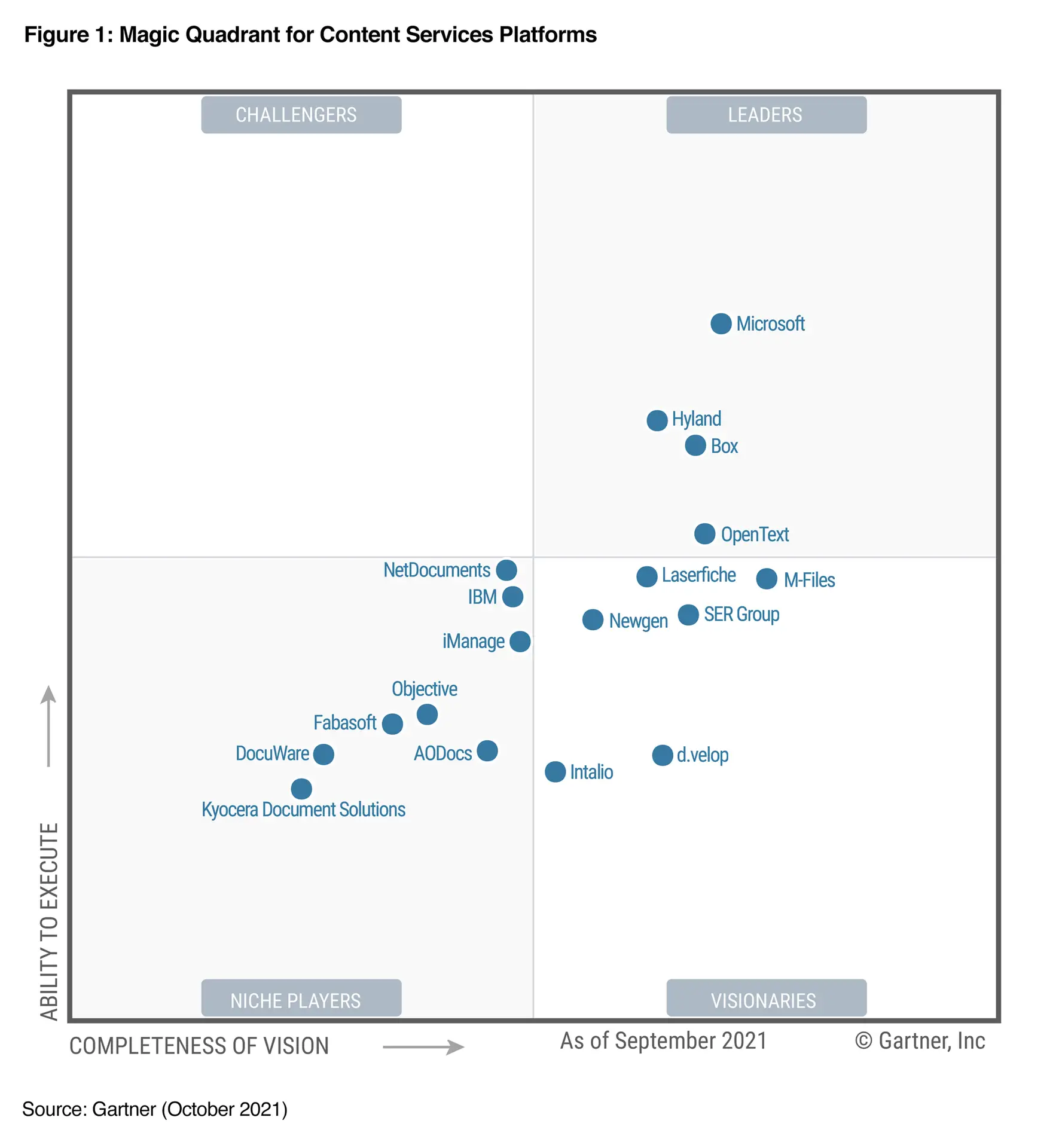
How to Read Gartner’s Magic Quadrants | Value, Limitations, and Practical Use for IT Leaders
Gartner’s Magic Quadrant is one of the most influential research tools for evaluating technology vendors.It ranks companies based on two key dimensions Ability to Execute (how well they deliver today) Completeness of Vision (how well they anticipate the future). However, while the Quadrant offers a useful snapshot of the competitive landscape, it can mislead when taken at face value.IT leaders should use it as a starting point for strategic evaluation not as the final decision-maker.True value comes from combining Gartner’s insights with hands-on testing, TCO analysis, and real-world fit to…
Read MoreHow to Plan and Execute a Seamless Office IT Relocation for SMBs
Planning an office IT relocation requires more than moving equipment it’s about rebuilding secure, stable infrastructure.SMBs must audit their current IT setup, preconfigure connectivity in the new site, label and back up every system, and validate performance post-move.A structured, step-by-step plan from cabling and power readiness to testing and optimization ensures minimal downtime and full business continuity. Strategic Planning and Infrastructure Assessment The most important step in any office move is planning, and in the IT domain this is especially true. Before dismantling a single workstation, SMB leaders must map…
Read MoreThe Critical Importance of Application Security | Addressing Emerging Threats
The Evolving Threat Landscape Recent developments in cybersecurity have underscored the growing risks associated with application security, as attackers continue to exploit vulnerabilities in enterprise applications, APIs, and cloud environments. With the proliferation of zero-day exploits and API-based attack vectors, organizations are facing an increasingly sophisticated threat landscape that demands proactive security measures. A recent study by Veracode revealed that over 76% of applications contain at least one security flaw, with nearly a quarter of them classified as high-severity vulnerabilities. These security gaps highlight the urgent need for enterprises to…
Read MoreChinese APT Exploits VPN Vulnerabilities to Target OT Organizations Worldwide
A New Cyber Threat Targeting OT Networks In a major cybersecurity alert, threat intelligence experts have discovered that a Chinese state-sponsored APT (Advanced Persistent Threat) group has been actively exploiting VPN vulnerabilities to infiltrate Operational Technology (OT) organizations worldwide. OT networks, which manage critical infrastructure like energy grids, water treatment facilities, and manufacturing plants, have become prime targets for nation-state attackers. The exploitation of unpatched VPN systems enables these threat actors to bypass traditional IT security controls, gaining direct access to sensitive industrial environments. This attack underscores the increasing risks…
Read MoreTop 5 Cybersecurity Threats Organizations Must Prepare for in 2025
The Evolution of Cyber Threats As digital transformation accelerates, cyber threats are evolving at an unprecedented pace. Attackers are becoming more sophisticated, leveraging AI-driven cyberattacks, supply chain vulnerabilities, and the convergence of IT and OT environments to exploit weak points in organizational security. Businesses—whether small startups or multinational enterprises—must recognize that cybersecurity is no longer an optional investment but a strategic necessity. This article delves into the five most significant cybersecurity threats of 2025, explaining their impact and outlining proactive measures that organizations must adopt to safeguard their data, operations,…
Read MoreGrok 3 | Elon Musk’s AI Powerhouse and Its Implications for the Future of AI
The Rise of Grok 3 in the AI Landscape The artificial intelligence (AI) industry is evolving at an unprecedented pace, with OpenAI, Google DeepMind, and emerging players like DeepSeek pushing the boundaries of AI innovation. In this highly competitive environment, Elon Musk’s xAI has introduced Grok 3, a next-generation AI model designed to challenge GPT-4o and Google’s Gemini models while offering unique features that set it apart. Grok 3 is not just another chatbot—it is built to deliver advanced reasoning, real-time search capabilities, and deeper contextual understanding. Integrated within the…
Read MoreHow to Join an Open-Source Project: A Guide for Developers
The Power of Open Source Open-source software has transformed the world of development, fostering collaboration, innovation, and community-driven progress. From Linux to Kubernetes, open-source projects power the backbone of modern technology, making them essential for developers looking to grow their skills and contribute to something meaningful. But how do you get started? What platforms should you use? And why should every developer consider being part of an open-source community? In this guide, we will walk through the fundamentals of joining an open-source project, the benefits, and the steps to becoming…
Read MoreWeb 3.0 | The Future of the Internet and Its Impact on Cybersecurity
The Evolution Toward Web 3.0 The internet has undergone several evolutionary shifts since its inception, from Web 1.0, which was primarily static, to Web 2.0, the era of social media and dynamic content. Now, we are entering the age of Web 3.0, a decentralized internet built on blockchain technology, smart contracts, and peer-to-peer interactions. For cybersecurity specialists and tech enthusiasts, Web 3.0 presents both opportunities and challenges. This article will break down how Web 3.0 works, its benefits, its security implications, and why it is revolutionizing the digital world. What…
Read MoreQuantum Cryptography: The Future of Secure Communication
The Next Frontier in Cybersecurity In the evolving landscape of cybersecurity, quantum cryptography stands as a revolutionary breakthrough, promising unbreakable encryption and next-generation secure communication. With the rise of quantum computing, traditional encryption methods are at risk, making quantum cryptographic solutions essential for safeguarding sensitive data against future cyber threats. This article delves into the world of quantum cryptography, its principles, real-world applications, and the impact it will have on cybersecurity, privacy, and global digital infrastructure. What is Quantum Cryptography Quantum cryptography leverages the principles of quantum mechanics to create…
Read More